Team AquaLink started off in the wrong direction. The team, part of a class at Stanford University called Hacking for Defense, was working on a problem for U.S. Navy divers, who work for sometimes 12 or more hours at depths of 60 to 200 feet. Currently divers have no way to monitor their core temperature, maximum dive pressure, blood pressure or pulse, which would provide early warnings of hypothermia or decompression sickness (the bends). The goal was to provide a wearable sensor system and apps that would allow divers to monitor their physiological conditions while underwater.
As they began to understand the SEAL divers' workflows and pains, Team AquaLink's members realized that providing health monitoring would just be a Band-Aid on a larger problem: The divers were spending greater periods of time than necessary underwater because of disorientation and inaccurate positioning. Moreover, the divers underwent many time-consuming and risky decompressions in order to surface to check their location. Team AquaLink decided to create a solution that would provide geolocation to the divers while they remained at depth. After interviewing more than 100 SEALs and other underwater experts and designing many minimum viable products (MVPs, a tenet of Hacking for Defense founder and instructor Steve Blank's Lean Startup methodology) to test their hypotheses, the team ultimately built and successfully tested a GPS buoy.
The members of Team AquaLink--Hong En Chew, Rachel Olney, Samir Patel and Army Maj. Dave Ahern, a Downing Scholar at the U.S. Military Academy at West Point's Combating Terrorism Center--were taking the pilot class of Hacking for Defense, a new DOD tool for solving problems.
The class grew out of an encounter in 2015 between a decorated Army colonel and a legendary Silicon Valley entrepreneur. Peter Newell, the managing partner of BMNT Partners LLC--a consultancy that brings together government and Silicon Valley groups to solve complex, critical problems--had retired in 2013 from a 30-year Army career, spending his last three years in uniform as head of the Rapid Equipping Force. (For more on BMNT, see "Speed and Urgency in Silicon Valley,") Steve Blank, who retired in 1999 from a 25-year career in Silicon Valley, was teaching his Lean LaunchPad entrepreneurship course at Stanford, and one of his students, a former Army Special Forces Soldier earning his MBA, advised him to meet Newell.
Newell and Blank were scheduled to meet for 30 minutes but ended up talking for more than three hours. Newell was trying to make Soldiers more lethal and safe. Blank was trying to help entrepreneurs build great companies. Each saw the overlaps in the other's approach. Both understood that the secret to innovation is not brainstorming sessions or whiteboards. Instead, innovation results from a disciplined and strategic approach to solving problems. Their joint brainchild is now known as Hacking for Defense (H4D).
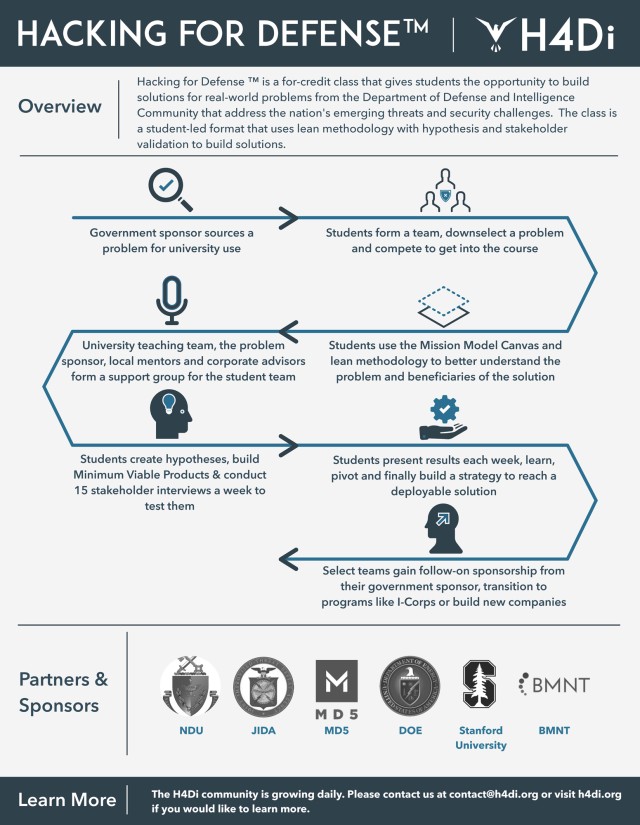
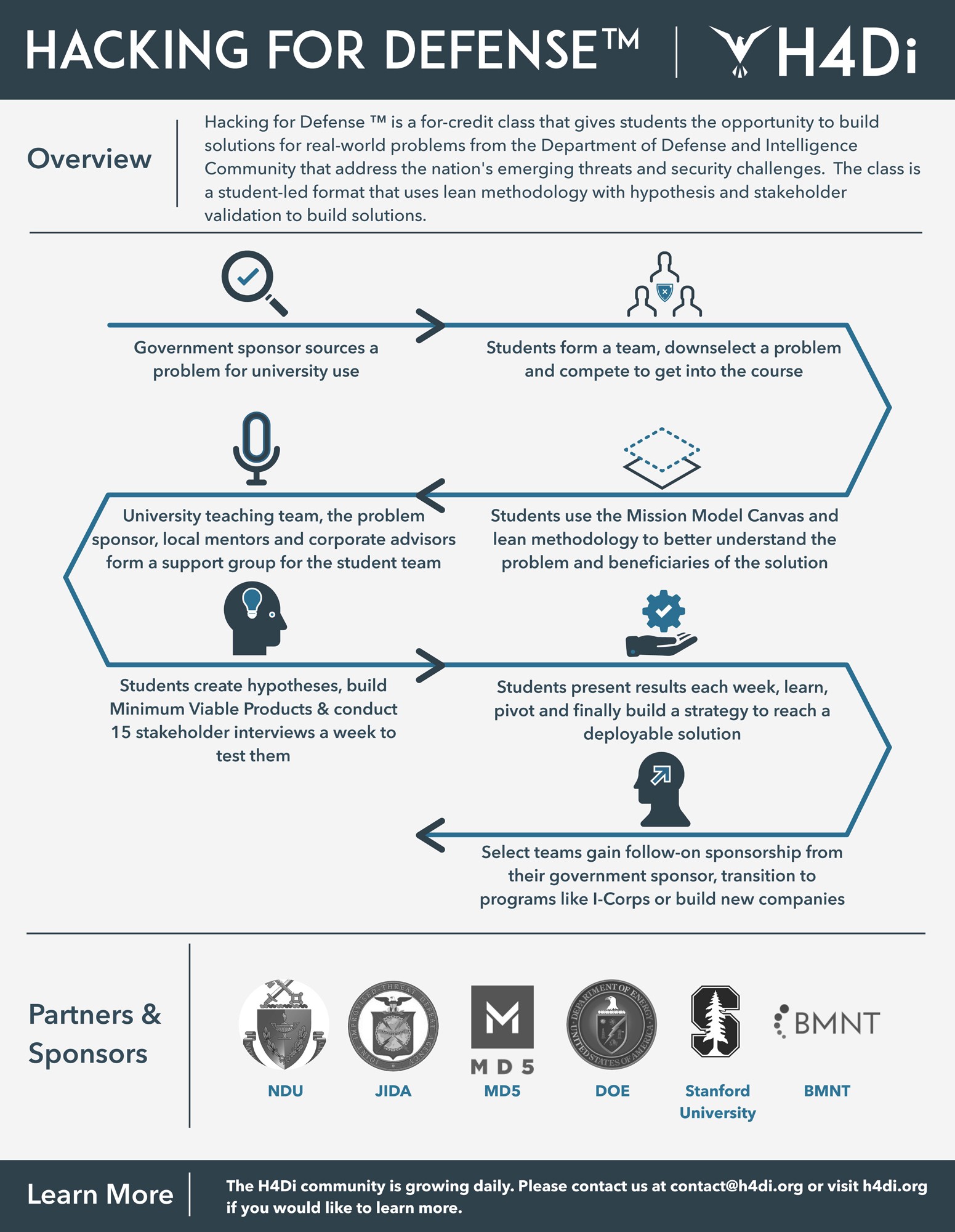
H4D--the methodology, and the class that teaches it--is on a mission to accelerate the speed at which national security organizations solve their problems. The core program is a 90-day process in which the customer works with BMNT to rapidly validate the understanding of a problem, recruit a coalition of users and partners to work on it, build MVPs to test the main aspects of the solution and develop pathways to quickly deploy what works.
The H4D approach has worked on automated orchestration in cybersecurity operations; data visualization for analysts; wearable medical devices; secure near-field networks; advanced manufacturing and rapid prototyping; underwater and airborne drones; and commercial space technologies.
H4D GOES VIRAL
Hacking for Defense rapidly expanded beyond BMNT's work with U.S. government agencies to include the class at Stanford. Since its pilot there in spring 2016, the H4D course has been expanding to universities nationwide in collaboration with MD5, the National Security Technology Accelerator, a partnership among DOD, New York University and other top U.S. research universities to promote civil-military technology cooperation. In addition, other courses are underway and in development to apply H4D methodology to problems associated with diplomacy, space and urban resilience--a collaboration with local, state and federal agencies to solve problems related to emergency response, disaster recovery, domestic relief operations, etc.
In the first step of program expansion, Stanford is currently offering a Hacking for Diplomacy course. (Secretary of State John Kerry paid a visit in October 2016.) Other universities that are holding or will soon offer Hacking for Defense courses include Stanford; Georgetown University; the University of California, San Diego; the University of Pittsburgh; James Madison University and Boise State University.
H4D is not easy work, for either sponsors or students. Sourcing a problem to H4D does not mean organizations get to hand off grunt work to Silicon Valley or academia. Sponsoring organizations are actively involved in the H4D process, whether by sending a team to BMNT or by facilitating interviews and MVP testing with their student teams. That means that organizations interested in solving tough problems through this rigorous process should make sure they are prepared for the workload.
Teams conduct dozens of interviews during H4D, questioning, breaking down and validating their problems. Participants are required to get in touch directly with operators and experts. And sometimes they even spend time wearing the gear and engaging in part of the mission.
AN IMMERSIVE EXPERIENCE
The first H4D at Stanford attracted a diverse group of students that included engineers, law students, MBA students, veterans and military fellows, and even foreign veterans. Students were drawn to the challenge of solving tough real-world problems, and applied their carefully honed technical and management skills in a high-pressure environment that replicated a fast-paced startup company. They were excited to work on problems well outside the academic sphere and relished the opportunity to perform a national service.
"As a student, you accept that only your grade reflects the impact of your hard work. H4D breaks that norm because you see your work making a difference for service members," said Sam Gussman, a member of Team Skynet during Stanford's H4D pilot. The class was a lot of work, Gussman said, "but opportunities like this are why I came [to Stanford]."
Students had to apply to take the class; from nearly 60 applicants, 34 were accepted. The students formed eight teams, each applying as a team to solve a specific government-sponsored problem. Accepted teams then prepared for their first class by interviewing 10 stakeholders--typically front-line military personnel experiencing the problem firsthand. During the next 10 weeks, each team interviewed between 100 and 150 users, tested countless hypotheses and prepared weekly presentations that demonstrated how fast the teams were learning about their chosen problem.
H4D motivated the teams to get outside the building to experience their challenges. For Team AquaLink, this meant gearing up in Navy dive suits. Team Right of Boom donned explosive ordnance disposal suits to experience impeded mobility, in order to determine the feasibility of a virtual tool to help foreign national military and law enforcement agencies counter improvised explosive threats. Team Skynet, working to increase the situational awareness of small tactical teams and reduce their cognitive load through the use of drones, simulated the cognitive strain of combat by running an obstacle course carrying 40-pound sandbags. Across the board, all teams invested time, sweat and tears to search for solutions.
CONCLUSION
H4D continues to expand, driven by demand for passionate and talented student teams to work on national security problems. Both the students and the sponsoring government organizations derive tremendous value from the intensive and challenging process. Several of the teams' solutions are going forward--some funded by private investors and others by government agencies--but that is not the point of H4D.
Students in an H4D course learn a new way of thinking about problems. What's more, they are able to experience national service in a unique way. H4D lets students work on difficult problems that affect the people who protect them. The students develop an empathy and affinity for the military, and many are now considering careers in national security.
In addition, participating government organizations learn the lean methodology alongside H4D students and gain a common language for innovation. Government participants and students also build relationships that will improve networking and collaboration, particularly as students build careers after graduating. These shared lessons and relationships are the essence of the H4D "Innovation Insurgency": training and educating current and future leaders in government, academia and industry with a goal of hardwiring the national security enterprise to solve mission-critical problems with speed and innovation.
For more information for universities and government sponsors interested in H4D, Georgetown University will host the next H4D Educators and Sponsors Course Jan. 17-19; email contact@h4di.org for details. For more information on Hacking for Defense Inc. (H4Di), go to http://www.h4di.org/.
This article will be published in the January - March 2017 issue of Army AL&T Magazine.
Related Links:
U.S. Army Acquisition Support Center




Social Sharing