FORT MONMOUTH, N.J. - The Communications-Electronics Research, Development and Engineering Center successfully matured and transitioned cutting-edge technology for securing battlefield networks, culminating with a successful demonstration at Telcordia labs in Piscataway, New Jersey June 26.
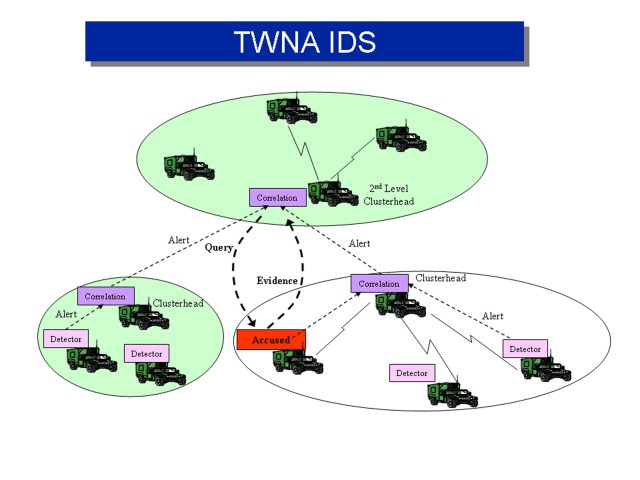
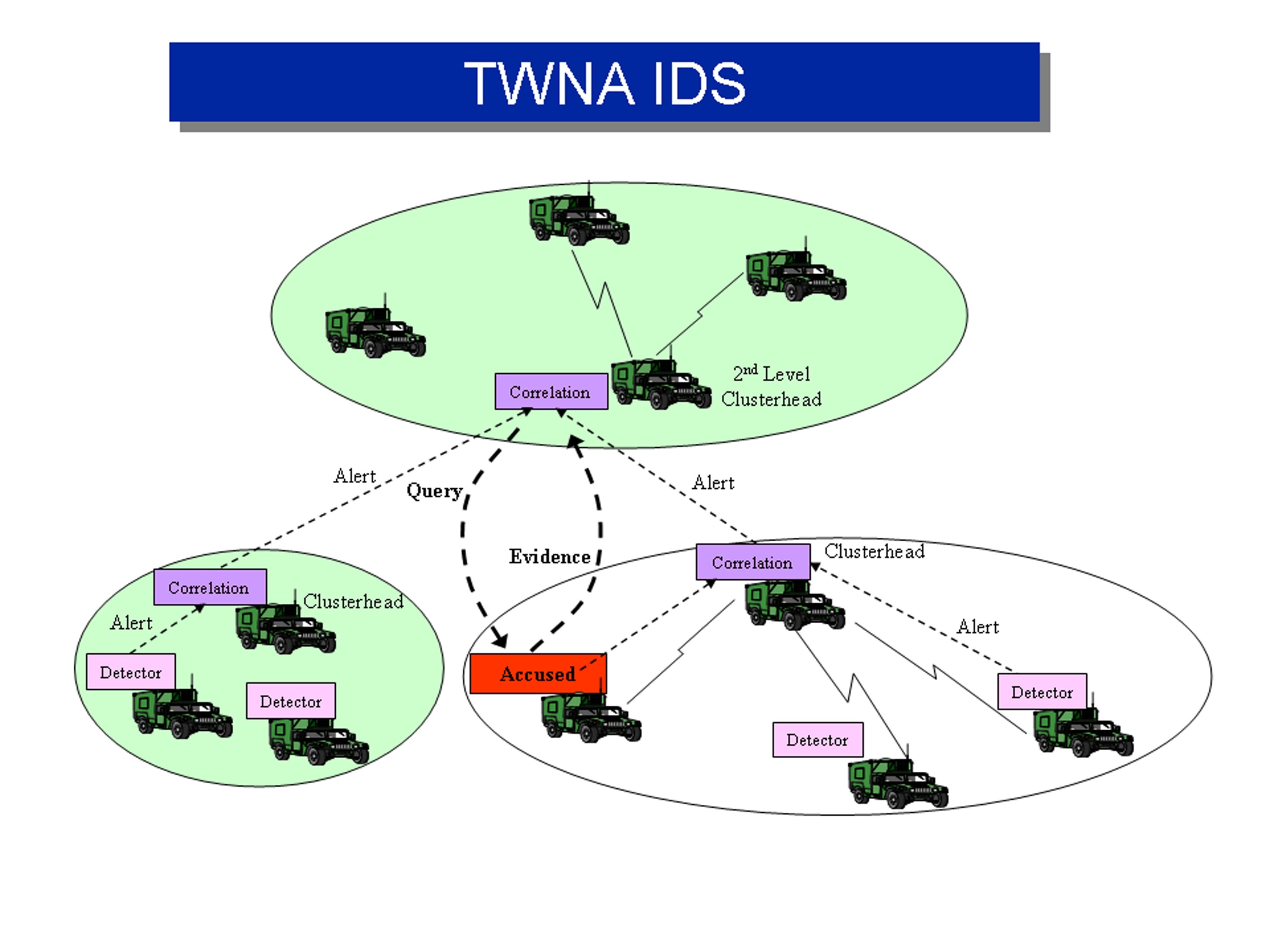
Security technology developed under the Tactical Wireless Network Assurance Advanced Technology Objective by CERDEC's Space and Terrestrial Communications Directorate's Information Assurance Program Director was transitioned to Program Manager Future Combat System Brigade Combat Team Network Systems' Integration after proving technology readiness level six. This satisfied the requirements of a Technology Transfer Agreement between the CERDEC and PM FCS (BCT) NSI to develop intrusion detection technology capable of detecting cyber-attacks against tactical mobile ad hoc networks.
A lack in wireless network security is a significant problem the Warfighter faces on and off the battlefield, said Shane Snyder, S&TCD computer engineer who has been working with the TWNA program since 2005. Networks can often be infiltrated causing a lapse in vital communication between commanders and troops. The TWNA project, which has been in development since 2003, is the premier technology working to better tactical network security through intrusion detection, said Snyder.
"The only way that a PM will take a technology from an ATO is if it is at TRL 6. What we were working on was intrusion detection, which was a critical technology. There are no commercial products like this, so it really fits a gap that they needed and we were able to transition it to them on time," said Snyder.
The intrusion detection determines when a network entity or node becomes malicious, stops it immediately and "removes it from the network," said Christopher E. Fleming, S&TCD computer engineer with the TWNA program. "It's important that the Intrusion Detection System is automated as much as possible so that the end-user, the Warfighter, will not be distracted from their mission."
TWNA provides many benefits for the Warfighter. It reduces system vulnerabilities, maintains Warfighter trust to provide secure information on the battlefield, efficiently monitors bandwidth to repair the clogging of networks due to malicious attacks, and works to prevent those attacks from adversaries.
Getting to this point was not without its challenges, said Snyder. "Going through the hurdles of software development, fixing a bug then changing something to add functionality and going back and fixing more bugs, was probably the biggest issue getting it up to a TRL 6," said Snyder.
TRL 6 requires a prototype demonstration in a relevant environment for further development. The June 26 presentation included numerous examples of network attacks, such as packet drops and wormholes, and how TWNA works to eliminate them automatically and efficiently.
With TWNA being transitioned to the PM FCS, CERDEC plans to further develop this technology under the Tactical Information Technology for Assured Networks, or TITAN ATO, to encompass a much broader form of network security.
"There's still some decent work to be done. TWNA was specific to a certain program so we're looking at a more general solution now," said Snyder. "We're looking at intrusion detection, cross domain solutions, public key infrastructure, and malicious code. It's networks, it's command and control, and it's battle command. It's a huge program."
Today's Warfighter relies on communication to complete the mission. Without automated tactical network security, troops would have to sit for hours on end and monitor networks for computerized attacks, said Fleming. Projects like TWNA and TITAN bring crucial computerized security to the increasing prevalence of network centric warfare, he said.
Social Sharing