
ADELPHI, Md. -- Through state-of-the-art machine learning techniques, Army researchers discovered a first-of-its-kind method to detect stealthy cyber attacks that attempt to evade the detection of firewalls and network intrusion detection systems.
The researchers, from the U.S. Army Combat Capabilities Development Command, now known as DEVCOM, Army Research Laboratory, the University of California, Riverside and Samsung Research America, proposed Context Learning-based Adversarial Protection, the first fully-automated, unsupervised machine learning solution to accurately detect and localize deep packet inspection evasion attacks.
These evasion attacks largely involve subtle manipulations of packets to cause different behaviors at DPI and end hosts to cloak malicious network traffic that is otherwise detectable, said DEVCOM ARL researcher Dr. Kevin Chan.
“With recent automated discovery, it has become prohibitively challenging to manually curate rules for detecting these manipulations,” said Prof. Zhiyun Qian from the University of California, Riverside. “Our machine learning based method is principled and based on the observation that prior evasion attacks exhibit themselves in sequences of packets that are uncommon in benign traffic. Therefore, our method applied the idea of “context learning” to capture such inherent features of the attack. The method is shown to be highly accurate against most types of the evasion methods.”
This research is part of the laboratory's Cyber Security Collaborative Research Alliance, spanning research within the alliance’s detection and learning for deception research areas.
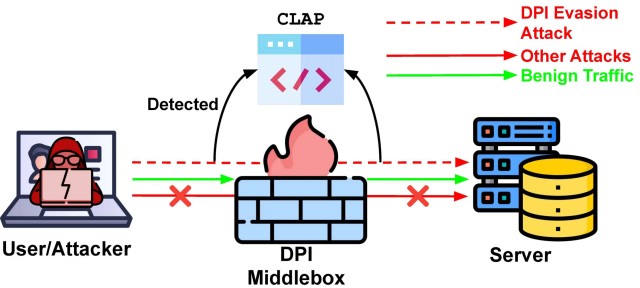
According to the researchers, prior work has been focused on developing handcrafted rules against these subtle sequences of packets that engage in evasion attacks, which does not scale to the numerous new evasion strategies being discovered. In this work, the research team automated the detection of such attacks, which overcomes the burden of manual intervention.
The contribution of this solution to the research community includes novel application of adversarial machine learning and machine learning techniques to learn the context of the information, where previous efforts were handcrafted and did not explicitly learn the context of the information, Chan said. Designing context-aware defenses increases the difficulty in successfully attacking these networks.
“[It] supports the Army’s Network modernization priority through improving the robustness and resilience of multi domain operations by advancing the state-of-the-art of detection of attacks on networked communications,” Chan said. “The research has strong potential to benefit the Soldier and as we move towards multi-domain operations, which will require greater interconnectedness and increased need to reliably exchange information.”
Moving forward, research will continue for the next two years as part of the eighth and ninth years of the Cyber CRA. The team will continue to work on increasing the robustness of Army networks through the novel use of machine learning.
Researcher virtually presented their paper, You Do (Not) Belong Here: Detecting DPI Evasion Attacks with Context Learning, the week of Dec. 1 at ACM’s CoNEXT 2020 - International Conference on Emerging Networking EXperiments and Technologies.
Visit the laboratory's Media Center to discover more Army science and technology stories
DEVCOM Army Research Laboratory is an element of the U.S. Army Combat Capabilities Development Command. As the Army’s corporate research laboratory, ARL is operationalizing science to achieve transformational overmatch. Through collaboration across the command’s core technical competencies, DEVCOM leads in the discovery, development and delivery of the technology-based capabilities required to make Soldiers more successful at winning the nation’s wars and come home safely. DEVCOM is a major subordinate command of the Army Futures Command.




Social Sharing