
ADELPHI, Md. -- A new data visualization approach developed by researchers working on an Army project may help cybersecurity experts detect, monitor and mitigate cyberattacks in a timely and efficient manner.
Depending on the task at hand, cyber defense analysts, cyber defense incident responders and network operations specialists often require different cybersecurity-specific visualization tools to process large volumes of alphanumeric data; however, according to researchers, creating a useful visual tool is not possible without an in-depth understanding of the tasks that these tools will have to perform.
Researchers from the University of Maryland, Baltimore County and Secure Decisions, a division of Applied Visions, Inc., collaborated with the U.S. Army Combat Capabilities Development Command’s Army Research Laboratory to design a procedure that extracts a cybersecurity subject matter expert’s internalized understanding of a dataset, so that it would be possible to create a 3-D data visualization tool that would enhance the SME’s ability to work with that dataset.
“For this project, we aimed to solve three loosely related problems,” said Kaur Kullman, a collaborating cybersecurity researcher at the Tallinn University of Technology in Estonia. “First, we needed to determine how to map the mental models that cybersecurity experts have already formed for their tasks. Then, we had to figure out how to create such visualizations that would align with the mental models that these experts use for sense-making of their data and be helpful for them in the process. Only then can we implement these specific visualizations in the software created for 3-D data visualization, and allow the experts to interactively explore their data, using these visualizations.”
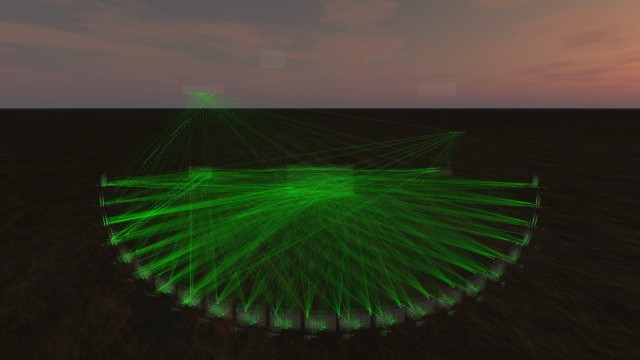
The mental model mapping method for cybersecurity, or the M4C method, that the researchers designed involves interviewing multiple cybersecurity practitioners and asking them questions about the properties that they seek within their dataset. These questions are specifically tailored to identify the relevant attributes of the dataset that help them form, verify or disprove hypotheses regarding possible incidents or noteworthy events.
For example, the interviewee is asked to identify the groups of entities that participate in a computer network and categorize the entities into logical and functional groups and subgroups. Through this process, the researchers can piece together the desired dimensions and structure of the data, such as the relations between identified groups, and the expected properties of grouped entities. Afterward, the researchers use the Virtual Data Explorer software to display the data in the layouts and data-shapes that were created based on the interviews.
“The M4C method can be used together with the software we’ve been creating for the past few years,” Kullman said. “Now network and security operation centers can create interactive 3-D visualizations of their data that can be experienced using mixed or virtual reality headsets.”
The 3-D data visualizations serve to provide contextual information to each element in the dataset so that users can explore and interact with the data more effectively. In addition, the application of stereoscopically perceivable 3-D may help individuals align their mental models with the raw cyber data to enhance their understanding of it.
“These visualizations are not geospatial, as overlaying a geospatial map with computer network traffic is seldom helpful for SMEs,” Kullman said. “Instead, the components of these visualizations are positioned spatially according to cybersecurity practitioners’ internalized understanding and expected relations of the entities usually found in their data.”
While it may take more time before the data source specific visualizations reach the point where they can suitably aid the users, these technical capabilities would be relatively inexpensive for the Army to employ. In addition, Kullman explained that further developments within this project would service the Army Modernization Priorities by enhancing the Army’s situational understanding in multi-domain operations.
This research collaboration has been in conjunction with the U.S. Army CCDC – Command, Control, Computers, Communications, Cyber, Intelligence, Surveillance, Reconnaissance Center – Sustaining Base Network Assurance Branch and the CCDC Army Research Laboratory - Network Security Branch. Together these branches have been using Kullman’s ongoing work for inclusion in the Virtual Reality Data Analytics Environment and Vids Data visualization engine respectively.
An upcoming project includes Kullman’s VDE visualizations as the first integrated analysis tool. It will leverage his current model and in the future use his research and procedure to support developing and integrating new models, he said.
“Once these capabilities are well-integrated into the arsenal of cybersecurity experts, their ability to maintain actionable situational awareness of Army networks will benefit significantly,” Kullman said. “Therefore, it is of utmost importance to provide the Army with a capability that would enable our cybersecurity experts to have qualitatively better situational understanding of the networked environments they need to protect.”
This research will be featured at the 22nd International Conference on Human-Computer Interaction. Information about the work, along with videos of some of the 3-D data visualizations, is available at this website.
CCDC Army Research Laboratory is an element of the U.S. Army Combat Capabilities Development Command. As the Army’s corporate research laboratory, ARL discovers, innovates and transitions science and technology to ensure dominant strategic land power. Through collaboration across the command’s core technical competencies, CCDC leads in the discovery, development and delivery of the technology-based capabilities required to make Soldiers more lethal to win the nation’s wars and come home safely. CCDC is a major subordinate command of the U.S. Army Futures Command.



Social Sharing