RESEARCH TRIANGLE PARK, N.C. -- High-frequency wireless signals may be more vulnerable to hacking than previously thought, according to U.S. Army-funded researchers at Brown University.
The research ("Security and eavesdropping in terahertz wireless links"), published in the journal Nature, demonstrates for the first time that a clever eavesdropper could intercept a signal from a terahertz transmitter without the intrusion detected at the receiver.
"This is the first investigation of security issues for terahertz wireless links, and it points the way toward improved security for terahertz communications," said Dr. Joe Qiu, manager of the Solid-State Electronics Program within the Engineering Sciences Directorate at the Army Research Office, an element of the U.S. Army Research Laboratory, located at Research Triangle Park in Durham, North Carolina.
Because of its higher frequency, terahertz radiation can carry up to 100 times more data than the microwaves used in wireless communication today, which makes terahertz more attractive than currently fielded tactical wireless networks the Army employs, Qiu said. Additionally, it has generally been assumed that these high-frequency waves would enhance security, as they travel in narrow, very directional beams, rather than the wide-angle broadcasts of microwaves.
"The conventional wisdom in the terahertz community has been that it's virtually impossible to spy on a terahertz data link without the attack being noticed," said Daniel Mittleman, a professor in Brown University's School of Engineering and a co-author of the research. "But we show that undetected eavesdropping in the terahertz realm is easier than most people had assumed and that we need to be thinking about security issues as we think about designing network architectures."
In microwave communications, an eavesdropper can put an antenna just about anywhere in the broadcast cone and pick up the signal without interfering with the intended receiver.
"Assuming that the attacker can decode that signal, they can then eavesdrop without being detected. But in terahertz networks, the narrow beams would mean that an eavesdropper would have to place the antenna between the transmitter and receiver. The thought was that there would be no way to do that without blocking some or all of the signal, which would make an eavesdropping attempt easily detectable by the intended receiver," he said.
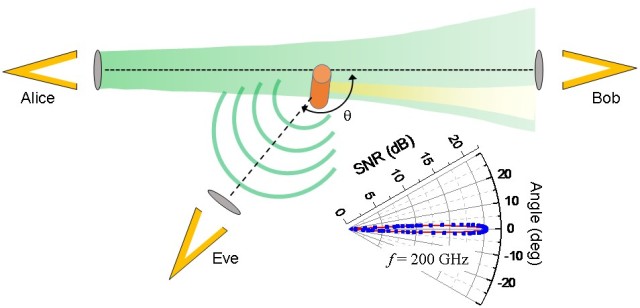
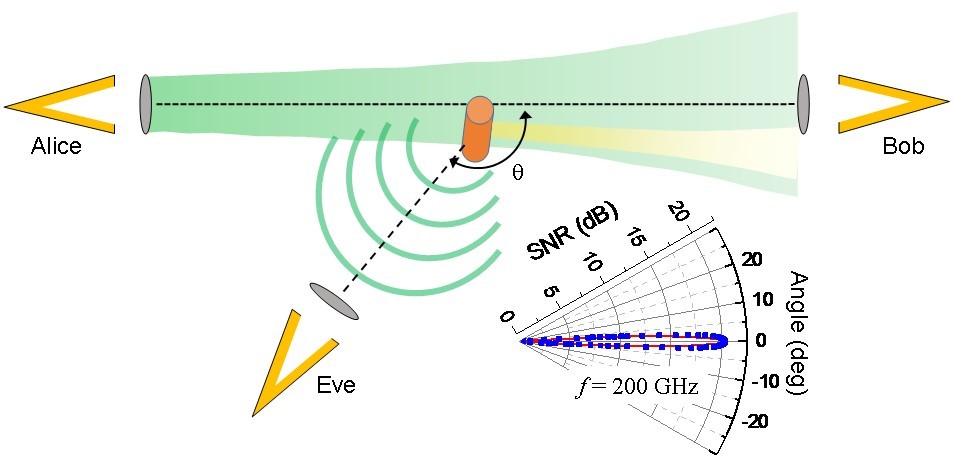
To test this notion, Mittleman and colleagues from Brown University, Rice University and the University at Buffalo set up a direct line-of-site terahertz data link between a transmitter and receiver, and experimented with devices capable of intercepting signal. They were able show several strategies that could steal signal without being detected--even when the data-carrying beam is very directional, with a cone angle of less than two degrees (in contrast to microwave transmission, where the angle is often as large as 120 degrees).
One set of strategies involves placing objects at the very edge of a beam capable of scattering a tiny portion of the beam. For a data link to be reliable, the diameter of the beam must be slightly larger than the aperture of the receiver. That leaves a sliver of signal vulnerable to an attacker without casting a detectable shadow on the receiver.
The researchers showed that a flat piece of metal could redirect a portion of the beam to a secondary receiver operated by an attacker. The researchers were able to acquire a usable signal at the second receiver with no significant loss of power at the primary receiver.
The team demonstrated an even more flexible approach (from the attacker's perspective) by using a metal cylinder in the beam rather than a flat plate.
"Cylinders have the advantage that they scatter light in all directions, giving an attacker more options in setting up a receiver," said Josep Jornet, an assistant professor of electrical engineering at Buffalo and a study co-author. "Given the physics of terahertz wave propagation, even a very small cylinder can significantly scatter the signal without blocking the line-of-sight path."
The researchers demonstrated an additional type of attack, involving a lossless beam splitter, that would be difficult, if not impossible, to detect. When placed in front of a transmitter, it would enable an attacker to steal just enough to be useful, but not enough to raise alarm among network administrators.
The bottom line, the researchers say, is that while terahertz links are associated with inherent security enhancements compared to lower frequencies, they are far from foolproof.
"Securing wireless transmission from eavesdroppers has been a challenge since the days of Marconi," said Edward Knightly, professor of electrical and computer engineering at Rice University and a study coauthor. "While terahertz bands take a huge leap in this direction, we unfortunately found that a determined adversary can still be effective in intercepting the signal."
________________________________________
The U.S. Army Research Laboratory is part of the U.S. Army Research, Development and Engineering Command, which has the mission to ensure decisive overmatch for unified land operations to empower the Army, the joint warfighter and our nation. RDECOM is a major subordinate command of the U.S. Army Materiel Command.
Related Links:
U.S. Army Research, Development and Engineering Command
Paper: Security and eavesdropping in terahertz wireless links
Social Sharing