Every networked system is subject to the risk of hacking and cyberattacks. Rarely does a week go by without news of an attempted or actual hacking of a government or private sector computer system. Cyberattacks against DOD and other parts of the government are constant--unclassified White House computer networks were breached in 2014, and the federal government employee records of 21.5 million people were stolen from the Office of Personnel Management in 2015. The U.S. Computer Emergency Readiness Team, part of the U.S. Department of Homeland Security, responds to hundreds of thousands of cyber incidents each year.
The Program Executive Office for Enterprise Information Systems (PEO EIS) is taking steps to prevent such attacks on the Army's General Fund Enterprise Business System (GFEBS), a networked system that processes financial and related transactions across the active Army, the Army National Guard and the Army Reserve. GFEBS includes integrated capabilities for financial management, managerial accounting and treasury disbursing, plus management of real property, plant maintenance and preventive maintenance and inventory. Have you ordered supplies, traveled on official business, received civilan pay or completed almost any other action that used Army general funds in the past five years? If yes, then you probably used GFEBS or someone used GFEBS for you.
The General Accountability Office (GAO), DOD, the Defense Information Systems Agency and the Army have issued information system and data protection guidance incorporating thousands of standards, attributes and business rules. The directives apply to federal systems and data in general and to federal financial systems and data in particular. The security guidance includes system access controls.
Controlling access to a system is one way of protecting it, and GFEBS achieves access control through the governance, risk and compliance (GRC) application. All individuals with access to GFEBS are vetted and approved using GRC. GRC, however, is only a tool. It requires continuing and timely actions by all GFEBS-enabled organizations to be effective. Those efforts are essential to controlling access and maintaining one element of cybersecurity.
A brief history of GFEBS highlights the need for governance, risk and compliance, and how the Army is positioned today.
EVOLUTION OF GENERAL FUNDS ACCOUNTING
Congress has expressed interest in improving financial management across the federal government since the 1980s. Congress after Congress passed measures aimed at raising accounting standards. However, progress was hampered by the fact that the primary accounting systems, i.e., the Standard Finance System and the Standard Operations and Maintenance Army Research and Development System, along with over 100 other specialized financial management systems, were nearly 40 years old and included hundreds of poorly documented patches. Maintaining and operating these systems was labor-intensive and costly; reports could not be quickly produced and the systems did not support a clean audit opinion by an independent public accountant, meaning DOD could not demonstrate that the financial statements were free of material misstatements.
The Army recognized the need to comply with the statutory, federal and DOD requirements, standards and business rules for achieving a clean audit. The Army also recognized the need for accurate, timely and practical information to improve decision-making in both the use of available resources to best support Soldiers and in programming and budget development to best support the Soldiers in the future.
The Army defined financial management requirements and explored potential solutions, concluding that an enterprise resource planning system would provide integration and traceability essential to a successful solution; DOD and Congress agreed.
After a competitive process, the Army awarded the General Fund Enterprise Business System integrator contract in June 2005. Two years later, Release 1 was completed and an initial pilot deployment occurred on Oct. 1, 2008. Over the next four years, a series of releases added content, and a series of deployment waves added thousands of civilian, military and contractor users at Army and other organizations worldwide. In July 2012, GFEBS attained full deployment status.
INTRODUCING GRC
The GFEBS pilot deployment was limited to about 250 end users, in a few organizations in a single command and at a single location with a few people from the headquarters office and Defense Finance and Accounting Service. The GFEBS team used manual processes, email and spreadsheets to manage the user access process. This manual process was time consuming and labor intensive for both the GFEBS team and the implementing command. The first GFEBS deployment involved 1,500 users in multiple organizations and at different locations and again relied upon a manual access control process. The difficulty posed by the manual process was intensified exponentially.
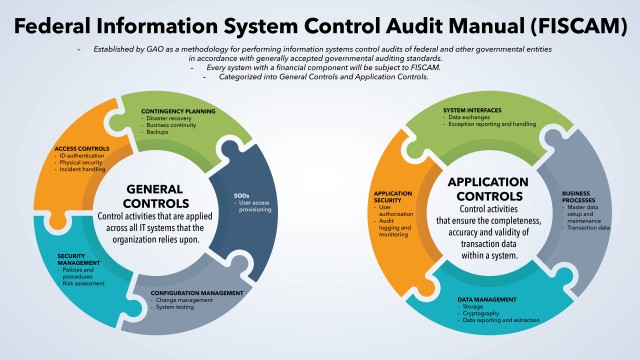
Knowing that subsequent deployment waves would involve 3,700 to 12,000 users, a more efficient access control solution--one that was integrated, net-centric, auditable and sustainable--was clearly necessary. The GFEBS program management office (PMO) explored commercial off-the-shelf options for a robust and efficient access control solution and selected SAP's GRC application. (See Figure 1.)
GRC provides an efficient means for the Army--the commands as well as the GFEBS team--to comply with mandatory audit controls for system access. The GAO's Federal Information System Controls Audit Manual (FISCAM) provides audit controls applicable to all federal financial management systems. The FISCAM is organized into general controls and application controls. The general controls apply to information technology systems; the application controls apply to the processes for data in the systems. Each control category is organized into subheadings with a series of specific critical elements that include control activities, techniques and audit procedures.
FISCAM controls for managing access to federal financial management systems apply equally to manual processes and automated applications. Pertinent FISCAM sections are provided in Figure 2.
GRC AND PROVISIONING
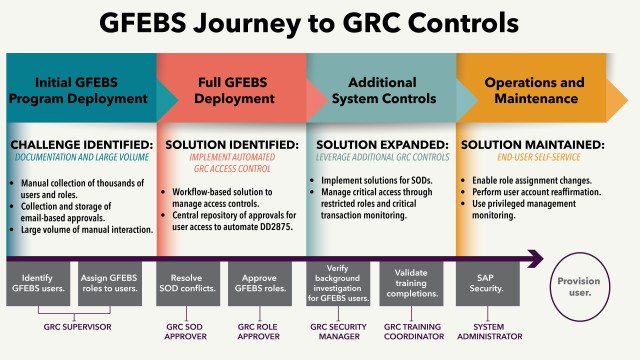
The GFEBS team determed the best solution to provisioning--the process of creating user accounts and providing appropriate access to those accounts--was a largely decentralized, automated workflow tool with well-defined processes. The GRC is a net-centric tool with standard processes and a central repository that enables distributed responsibilities and direct provisioning into GFEBS. DOD security technical implemenation guides require that provisioning of system users be approved using a DD Form 2875, a system authorization access request, or its equivalent. Every service member, U.S. citizen, local national employee and contractor requiring access to GFEBS must be provisioned. More than 100,000 users spread out across the world have been provisioned to GFEBS through the GRC tool.
The GFEBS provisioning process begins with explaining the GRC tool and process and the GFEBS user roles to each supervisor in the implementing organization. Supervisors are responsible for assigning GFEBS roles to each user, obtaining formal approval and entering the user's electronic data interchange personal identifier and assigned roles in GRC. GRC transmits the data to the Army Management Learning System (ALMS), which identifies training for each role for each user. ALMS records completed training and transmits that data back to GRC, where the training coordinator acknowledges the training completion. Additionally, the local security manager confirms the appropriate positively adjudicated background investigation in the Joint Personnel Adjudication System. For non-U.S. citizens, the security approval process depends upon various criteria such as terms in the Status of Forces Agreement, whether the individuals are direct or indirect hires and specific GFEBS roles.
The GRC tool and process provides:
• A systematic approch for managing GFEBS access by the commands, PMO and functional office that mimics the approval elements found on the DD Form 2875.
• A standard, Armywide way of granting users access to GFEBS.
• A well-defined, rigorous and mature process consistent with audit controls for consideration in other Army, DOD and federal SAP applications.
The maturation of the GRC process is summarized in Figure 3.
GRC AND LIMITING AN INDIVIDUAL'S ROLES
In addition to controlling system access, other mandatory audit controls involve limiting actions by an individual, meaning no one can have both GFEBS initiator and approver roles for the same transaction. Known as a segregation of duties (SOD), this step maintains data integrity and protects against errors and fraud. (See Figure 4.)
The GRC tool uses risk analysis to identify role conflicts that would be a SOD, such as purchase order processor and invoice processor. Every conflict must be cleared before final provisioning. Clearing involves the implementing organization re-assigning user roles to remediate every SOD conflict. If remediation does not work, the organization may seek a waiver from the authorizing agency at DA; however, waivers are rarely granted and only for exceptional circumstances.
OTHER GRC BENEFITS
The GRC application provides an efficient means for accomplishing and managing the provisioning process. GRC accomplishes the routing from initiators to approvers, training and security administrators----important capabilities given that GFEBS is used by hundreds of thousands of people at more than 30 commands and other organizations around the world. The workflow functionality occurs seamlessly within the commands; between the commands and the GFEBS team; and between GRC and the Army Knowledge Online Lightweight Directory Access Protocol and ALMS.
POLICIES AND PROCEDURES
GRC systematically records and transfers provisioning data, checks for SOD and training completions and provides status for individual users. But GRC is only a tool, and like all tools, users need to be trained on how to operate it. Over the years, the Army has developed, refined and augmented policies and procedures to capitalize on GRC's capabilities and meet compliance requirements. In managing all access to the operational environment, GRC remains as important today as during initial fielding.
The GAO FISCAM and DOD and Army regulations are as applicable in the operational environment as during deployment. The GFEBS team has issued various policy guidance that address the command, the command's GRC authorizer and approvers, and the user's duties to act to control access to GFEBS, including the following:
• Commands or other user organizations must update user access priviledges within two days of a change in a user's status--when a user moves to another position and no longer requires some or all their roles, for example, or requires different roles. Every organization must withdraw access when a user departs from the organization; conversely, every organization must comply with the provisioning process when new military or civilian personnel join the organization.
• The GFEBS user must actively access the system every 45 days. If a user is inactive for more than 30 days, the system produces an email warning of a potential inactivity lock, Another notice is issued a week before the inactivity lock. If the user fails to act, the user is locked out. If the user remains inactive for 120 days, the user's roles are deleted from the system. A subsequent re-activation requires an unlock request and a change request to re-enable roles.
• GRC supervisors must reaffirm users and their roles each year. The GFEBS PMO creates reafirrmation requests in GRC for all registered users and supervisors, and GRC supervisors and role approvers must affirm the users in their systems. Failure to close the reaffirmation request results in the user's account being locked.
These actions are not busy work for the commands, supervisors or users: they are to comply with the mandatory requirements of the various governing regulations and, more importantly, to contribute to the security and protection of Army data from cyberattacks.
MANAGING RESTRICTED AND PRIVILEGED ROLES
Some GFEBS users require accesss to do more than typical GFEBS users do; therefore, GRC supports grannting and managing restricted roles to a small, very select group. Some restricted roles pertain to maintaining control over master data that is maintained exclusively by the Army Budget Office or the deputy assistant secretary of the Army for cost and economics, or certain certification functions limited to users with those job requirements.
Any system as large and as diversified as GFEBS also requires a select group of "superusers" with special privileges, and GRC also supports granting and managing these roles. (See Figure 5.) Their elevated access privileges come with unique capabilities to investigate, analyze and remedy critical and high-risk problems and the ability to monitor access to the system. Their actions are tracked, stored, monitored and reviewed. These roles are highly controlled and limited to a very small number of users in the PMO staff.
AUDIT SUPPORT
GFEBS is the Army's core financial system for supporting the Army's audit in FY18. Being auditable requires accurate, complete and timely data in the accounting system and well-documented business processes. Achieving this requires the active participation and integration of efforts by the staff of the assistant secretary of the Army for financial management and the comptroller, the GFEBS PMO and system integrator, the commands and virtually every user. (See Figure 6.)
CONCLUSION
GFEBS, like any system, is subject to hacking and cyberattacks. Controling access is one of the most basic means of protecting any system and data. GRC is an important tool for controlling access to GFEBS. But like all tools, it requires appropriate use by those who employ it.









Social Sharing