By KEN PRUITT, AMRDEC Cyber Lead
Everybody knows that cyber threats exist, that systems have vulnerabilities, and that the interaction of the two has consequences. The question for the Aviation and Missile Research, Development, and Engineering Center, and the weapon systems we design and support is, "How do we deal with those threats, vulnerabilities and consequences?" Defining these terms from a weapon system perspective is helpful in answering this question.
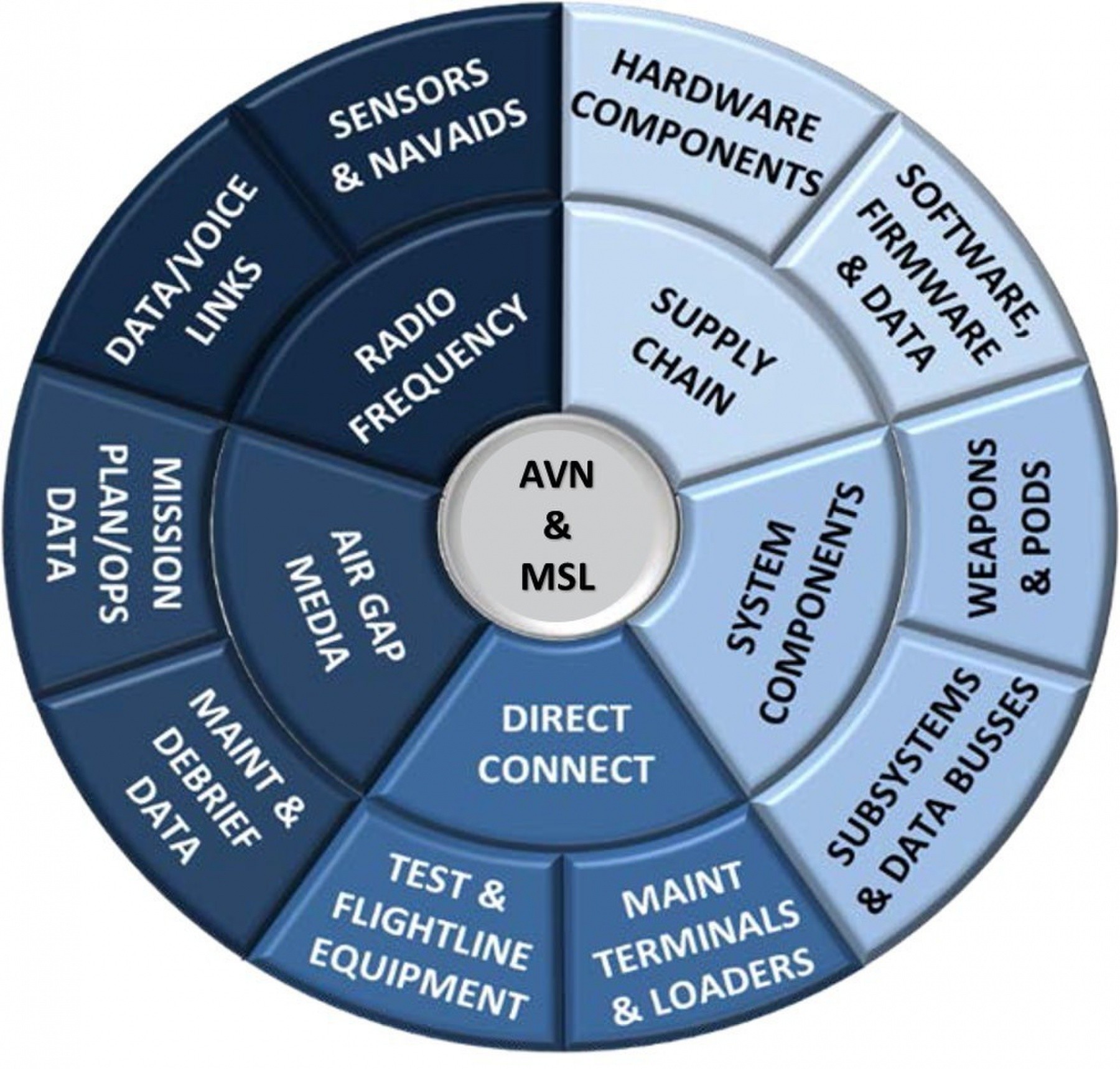
A threat can be defined as any technique used by an adversary to exploit vulnerabilities in order to acquire system information or disrupt/degrade system performance. Vulnerabilities are found in programs, organizations, personnel, networks, systems and supporting systems. They take the form of inherent weaknesses in hardware and software that can be used for malicious purposes; weaknesses in processes that can be used to intentionally insert malicious hardware and software; and unclassified design information within the supply chain that can be aggregated.
The consequences of compromised vulnerabilities have negative impacts to the weapon system (corruption and disruption) and the mission (capability is countered or unable to fight through), and ultimately the loss of technological advantage.
A high priority for AMRDEC is developing a strategy for creating cyber resilient weapon systems. Cyber resilience has been defined as "ensuring mission success in a cyber contested environment." The problem of cyber resilience can be further clarified with more questions. What do we do for existing, fielded weapon systems? And, what do we do for weapon systems under development?
At AMRDEC, the answers to these questions are addressed by two cybersecurity goals. First, "bake-in" cyber resilience in new weapon systems. Second, mitigate "critical" vulnerabilities in fielded weapon systems. Baking-in cyber resilience is the capability to systematically design, test, field and sustain cyber resilient weapon systems. Mitigating vulnerabilities requires system weaknesses to be identified, impacts to be validated, risks to be assessed and solutions to be implemented.
There are currently two AMRDEC activities designed to specifically address these goals. First, AMRDEC's Cyber Science and Technology efforts concentrate on both goals. Most AMRDEC S&T initiatives are developing technologies and capabilities that will allow future weapon systems to dynamically detect and mitigate cyber and electromagnetic activity attacks. Among these are the CEMA Algorithm (internal system centric), the Tactical Datalink Cyber Detector (datalink centric), and the RF-enabled CEMA Defense Techniques (radar centric) development efforts.
Several S&T efforts are also intended to directly address critical fielded weapon systems, or to support the on-going evaluations of fielded systems under the fiscal year 2016 National Defense Authorization Act Section 1647 requirement. Among these are the Supply Chain Assessment Tool, CEMA Effects Injection, and MIL-STD 1553 Cyber Defense projects. An important side-effect of all AMRDEC Cyber S&T projects is the continued development of a cyber-savvy workforce capable of integrating cybersecurity and cyber resilience measures into all phases of the acquisition process.
AMRDEC is directly supporting assessments focused on finding and mitigating critical vulnerabilities in fielded systems. A detailed process has been defined to facilitate this activity. The objective of this process is to provide only validated vulnerabilities for a given weapon system, should they exist. The next step will be to develop mitigations for those vulnerabilities.
These activities are only two of the key cyber capabilities underway at AMRDEC that address the development of cyber resilient weapon systems. As the AMRDEC Cyber Strategy continues to evolve, new capabilities will be added to better meet the needs of our customers from a systems security engineering and cybersecurity perspective.

Social Sharing